Broadcasters, equipment manufacturers and other experts have made suggestions to the FCC about improving operational issues and security for EAS.
Several subgroups of an advisory committee, the Communications Security, Reliability and Interoperability Council, met yesterday and reached several conclusions.
Regarding potential improvements since the 2011 national EAS test, the group has several recommendations, including:
● Use event code “NPT” for National Periodic Test, to enable automatic generation of text for national level tests. Unlike an Emergency Action Notification, NPT specifies “test” to reduce confusion.
● Use NPT up to twice a year, replacing the Required Monthly Test in those tests. But keep the NPT to two minutes.
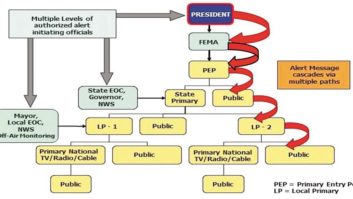
● Use the EAN, which is activated by the president or his/her representative, once every three years to test.
● Adopt the national location code (000000) for both EAN and NPT to prevent confusion with a specific city code and to prevent firmware from adopting a new location code.
Monroe Electronics Senior Director — Strategic Development & Global Government Affairs Edward Czarnecki is on CSRIC and tells Radio World that it’s up to the FCC as to how to address the recommendations. Many do not require a rulemaking, just a clarification, according to the group.
CSRIC made recommendations for cybersecurity enhancements to EAS as well. Czarnecki is involved with this working group.
The recommendations go beyond telling broadcasters to place their Internet-connected encoders/decoded behind a firewall with password protection, advice the agency made last year, by suggesting adding controls for accessing user accounts, software updates and physical equipment security. The group had recommendations for manufacturers and alert originators as well. “Coordination and collaboration between the EAS participants, device manufacturers, alert originators and the government will reduce the likeliness of EAS being compromised,” notes the group in its report. The experts add the caveat that the report is just a starting point that should be reviewed regularly as cyberthreats evolve.