This year, let’s all give each other festive analog holiday gifts, shall we?
Not to sound like a fusty Ebenezer Scrooge, but the popularity of insecure Internet of Things devices and Apple’s decision to remove an analog headphone jack from their latest iPhone product make your obedient engineer murmur “Bah, Humbug” into his stocking cap. (Wag and showman-who-won’t-harm-you Stephen Colbert observed about the wireless AirPods that Apple has now invented earphones that are even easier to lose.)
Given that they’re unavailable as of early December, they require a power source to charge and they’re slated to cost $159 once they’re on the market, one may ask, “Have industrial designers gone mad?”
Analog audio is the universal medium, the go-to that can connect almost any output to almost any input — it’s the easiest, least expensive way to get audio out of a consumer device — and has been reliable for over a century. In that vein, imagine if Thomas Edison had held production while he developed a Bluetooth-enabled cylinder phonograph.
In radio broadcast, analog audio is on the ends of the alligator clips, waiting to be quickly connected in a pinch to solve that last/first mile failure. That a world class purveyor of must-have products (see Reference [1]) would remove this ubiquitous standard and replace it with an expensive wireless alternative is stunning … unless of course the removal of the analog jack and electronics is to make room for a good FM chip set, in which case I will soften my opinion.

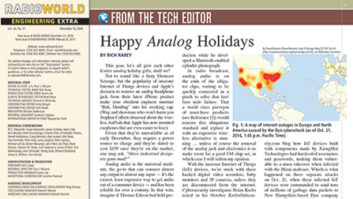
Fig. 1: A map of internet outages in Europe and North America caused by the Dyn cyberattack (as of Oct. 21, 2016, 1:45 p.m. Pacific Time).
By DownDetector (DownDetector Level 3 Outage Map) [CC BY-SA 4.0 (http://creativecommons.org/licenses/by-sa/4.0)], via Wikimedia Commons With the insecure Internet of Things (IoT) devices, we’re stuck with these hacked digital video recorders, baby monitors and IP cameras, unless they are disconnected from the internet. Cybersecurity investigator Brian Krebs noted in his October KrebsOnSecurity.com blog how IoT devices built with components made by XiongMai Technologies had hardcoded usernames and passwords, making them vulnerable to a mass takeover when infected with the Mirai malware. Which is what happened on three separate attacks on Oct. 21, when these infected IoT devices were commanded to send tens of millions of garbage data packets to New Hampshire-based Dyn company networks. Dyn and other companies provide internet-critical Domain Name Service (DNS) so that humans can conveniently enter words into a browser (“google.com”) instead of an internet protocol address (“216.58.217.78”). The IoT devices flooded Dyn with an estimated network load of 1.2 terabits per second, bringing connectivity to a halt. Communications company Level3 published a world map (Fig. 1) showing the most severe outages in the United States, with European countries less affected. On Nov. 25, another distributed denial of service attack was targeted at the legislative arm of the European Union — the European Commission — which was shuttered for an afternoon because its internet connectivity was essential for its work.
THANK YOU, RICH, AND WELCOME, CRIS!
From Editor in Chief Paul McLane:

Rich Rarey Rich Rarey, who has served as technical editor of Radio World Engineering Extra for the past two years, is leaving the position after this issue to devote more time to his consulting business, Rareworks LLC, where he works with companies like Tome Inc. developing novel drone software for search and rescue work, as well as creation of in-car high-resolution audio systems; and Jump2Go, developing a broadcast-based national alerting system. He’ll continue to be a valued contributing author in RWEE. Thank you Rich for your superb work, your engineering insights and your fabulous sense of humor.

Cris Alexander I’m pleased to announce that Cris Alexander will take the tech editor’s reins starting in February and is already planning that issue’s contents. A longtime member of the Radio World family, W.C. Alexander started his broadcast career in the mid-1970s, working in both radio and television stations before settling into a radio career and coming to work for Crawford Broadcasting Co. as director of engineering in 1984, where he has overseen its growth from six stations to a nationwide entity. He is managing partner of Au Contraire Software, which produces moment-method modeling and AM/FM design software. He is active in the Society of Broadcast Engineers and holds CPBE, AMD and DRB certifications.
Like Rich and our founding Technical Editor Michael LeClair, Cris will perform the role on a contract basis while keeping his busy day job. Reach him at [email protected].
Radio World Engineering Extra recently noted our 12th anniversary, while Radio World itself turns 40 next summer. Cris and Rich have both been important reasons for the success of these publications. I thank them as well as you, our reader, and the sponsors whose support has made this publication possible. Here’s to many more!
How do these attacks affect broadcasters? Certainly securing online broadcast-critical devices with strong passwords and disabling unused network ports at the station’s firewall is a start for self-protection, suitable for reducing the risk someone can hijack your transmitter, RBDS or HD Program Service Data, but when the internet itself is brought down it reveals the false cost-savings of a public internet-based studio-to-transmitter link. One station group I worked with used the public internet to reach its far flung transmitters, and on any given sunny day, the public internet was a fine, inexpensive STL. When the service failed, however, the local internet service provider couldn’t or wouldn’t expedite trouble tickets, and the station remained off the air for extended periods. There were several possible solutions, none as inexpensive as the public internet: Make the primary audio path a satellite-delivered data service with backhaul; or make the primary path a leased and dedicated point-to-point fractional T1 circuit with a codec at studio and transmitter. The last time I checked they were considered keeping the public internet but installing an analog telephone line with a POTS codec as a backup.
As mentioned elsewhere in this publication, I am stepping aside as your technical editor and am delighted that Cris Alexander is assuming the role. It has been a pleasure learning about radio broadcasting all over again from the authors and readers through the last two years. Editor in Chief Paul McLane deserves a big shout-out for his calm guidance and superb editorial sense, and Production Manager Karen Lee transforms our puny typing efforts into an elegant, visually pleasing publication. I literally could not have done it without them.
REFERENCES
[1] Apple device fanatics: You know who you are.