Cybersecurity, unlike other projects around the station, is never finished. It requires ongoing diligence to be ready for threats that are constantly changing.
Wayne M. Pecena, CPBE, 8-VSB, ATSC3, AMD, DRB, CBNE, is associate director of educational broadcast services at Texas A&M University’s KAMU FM/TV.
“Last year I would have said denial-of-service attacks were the greatest threat, but today it would be ransomware,” he said. That was in mid-2021. It can change, and change again.
Pecena is author of a paper submitted to the NAB Show Broadcast Engineering and IT Conference, titled “Can I Really Protect My Broadcast Plant from a Cybersecurity Attack?” It introduces the principles of cybersecurity, discusses how to protect the broadcast infrastructure and offers some action tasks.
This article summarizes that paper.
In the Beginning
Over the past two decades, Wayne Pecena wrote, the broadcast plant has migrated from an analog point-to-point infrastructure to an IT-based system that offers greater flexibility, more features and lower cost. Along the way, it turned into an Information Technology (IT) infrastructure, based upon the Internet Protocol (IP) for interconnection.
In many ways, it is like any other network, but the broadcast plant also contains servers that capture, process and playout content, as well as a cadre of host devices that provide the specialized services required in the broadcast workflow.
All those advantages come with a price. The same openness that makes it so flexible also enables hackers to easily get in and cause havoc. Those threats are numerous and widespread.
From a high-level view, they can be categorized into malware or network focused threats.
Malware threats focus upon the host operating system and applications they execute. Common industry sub-categories of malware include ransomware, viruses, worms and trojans, and spyware.
Network-focused threats target the network infrastructure components and exploit the IP protocol(s). They can include Address Resolution Protocol (ARP) spoofing, rogue service advertisements, Denial of Service (DoS) attacks, Distributed Denial of Service (DDoS) attacks and “Man in the Middle” attacks.
While the most dangerous threat is always a moving target, today it seems to be DDoS and ransomware. These many attacks can also come from several sources, including nation states, terrorist groups, organized crime, hacktivists, hackers and disgruntled individuals.
The sheer number and diversity in the type of threat sources make it essential to have an action plan and follow it. In order to get there, one must first understand a few cybersecurity principals followed by a structured approach to implementing prevention measures.
Pecena noted that the question is sometimes asked, “Can you make a broadcast plant 100 percent bulletproof in terms of cybersecurity?” He says absolutely — just remove all equipment that has an Ethernet connector and go back to analog gear.
Other than that drastic step, nothing is perfect, although a well-thought-out plan goes a long way towards mitigating the threat.
Principles of Cybersecurity
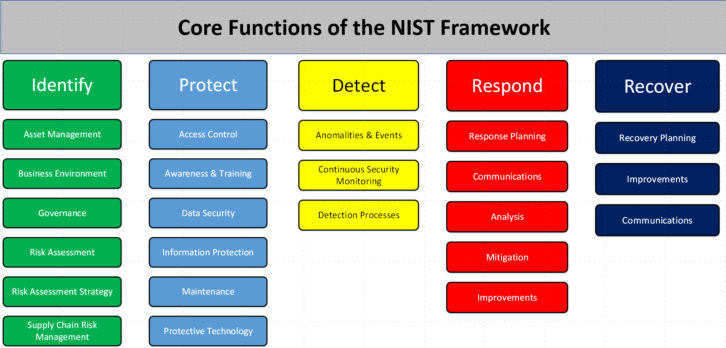
Fortunately for us, most of the groundwork for this topic has already been laid out by the National Institute of Standards and Technology (NIST). Their Cybersecurity Framework provides structured guidelines and steps to implement and maintain ongoing cybersecurity programs in any organization.
Five categories describe the high-level functional areas of a cybersecurity program, identify, protect, detect, respond and recovery. Additional granularity is provided by subcategories, each with its own set of reference documents.
The first function, identify, begins with a complete inventory of IT assets, including hardware, software, networks and data. From the inventory produced, the assets are in turn prioritized based on an organization’s business needs. For broadcasters, any assets involved in the reliable delivery of program content should get top priority. Less priority is assigned to the lower impact threats. A numerical rating scale is often used to describe the overall cybersecurity health of an organization’s IT systems. Areas found deficient can then be used to prioritize resources to remedy or bring into compliance in situations where regulatory requirements or organizational policy exists.
The second function, protect, utilizes the previously compiled IT asset inventory to create a policy or approach of what to protect and how to protect an asset. It is addressed in terms of physical asset protection as well as establishing access control for users and applications. The concept of least privilege required is utilized.
Thirdly, the detect function is focused upon IT asset monitoring, knowing what is normal and what is not, and sounding an alarm when an anomaly occurs. Necessary monitoring devices are identified in this step.
Fourth, the response function is a plan for when a breach occurs. This may be anything from a physical event such as a break in to a malware incident. A recovery plan should be developed in advance to ensure a return to normal as quickly as possible. This is a better alternative than developing a plan after an event occurs. The post-analysis aspect of any event occurrence is an important step in continuous improvement.
Finally, recover entails implementing the above-mentioned plan. Following the outlined steps should restore compromised assets and a return to normal operations.
A deeper dive into the protect function is available through the principal of Defense in Depth (DiD). Developed by the National Security Agency, its goal is creating multi-layered coordinated security mechanisms to provide redundant levels of protection.
Pecena says examples of DiD mechanisms found in IT infrastructures include physical access barriers, segmented (layered) network architecture, ethernet port security and packet filtering through an Access Control List (ACL).
To further clarify the access portion of the protect function, the Principle of Least Privilege (PoLP) is applied. Through the use of access controls, the system grants the minimal resources required for a user or an application to the perform the desired system function. An example would be allowing on authorized users to access specific systems or an application to have file modification permissions.
The CIA triad is another classic model of IT security. It utilizes three objectives to be achieved within any IT system ranging from the network to the server storage systems to the applications. They are Confidentiality, Integrity and Availability.
Confidentiality entails preventing information from reaching undesired hands or unauthorized users. Access by users and applications is restricted or limited to a “need-to-access.” Other implementation techniques include encryption, authentication and off-line data storage.
Integrity seeks to prevent data being changed as it moves through a network, is processed through an IT workflow or archived in a data storage system. Implementation mechanisms include file access controls, checksums and encryption. An important aspect of the Integrity objective is to have detection mechanism(s) to know if data has been if tampered with or altered.
Availability seeks to insure that IT resources are available to legitimate users or applications and not available to those who are not authorized. Implementation techniques include network infrastructure redundancy, server redundancy and attack detection systems.
Despite the CIA acronym, Pecena reminds us that this security model has nothing to do with the U.S. Central Intelligence Agency. To avoid confusion, the order is sometimes changed to AIC.
The CIA triad is also used as a roadmap for those seeking to do harm to IT systems and broadcast plant operations. In these instances, Confidentiality becomes a target to be breached to obtain valuable information through techniques such as social-engineering or spyware. Integrity may be compromised through Man in the Middle attacks, malware and data record manipulation. Availability becomes the primary objective of a ransomware infection or a Denial of Service (DoS/DDoS) attack.
Protecting Broadcast Infrastructure
At a high level, the overview of an organization’s IT infrastructure can be divided into three areas, each with unique cybersecurity needs. These are the network, hosts device and applications.
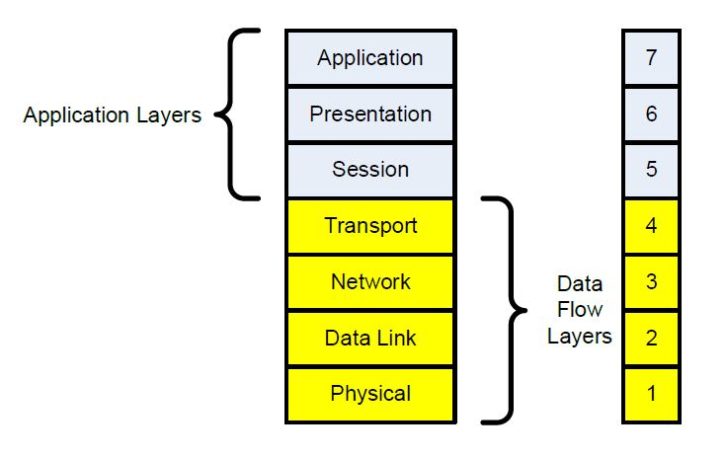
The Open Systems Interconnection (OSI) model developed in the early 1980s is the classic model that describes how host devices communicate with each other over a network. This model provides an excellent structure in which to implement cybersecurity precautions. The first four layers of the model are referred to as the data-flow layers and are associated with the network functions.
Layer 1 or the physical layer of the OSI model is associated with the physical type of network deployed. Options are Ethernet-based and include wired through twisted-pair copper cabling, fiber optic cabling, wireless or a combination of all three in many networks.
From a security standpoint, the physical layer can also be applied to physical security of the network infrastructure equipment. Implementation strategies can include locked wiring closets, equipment cabinets and rack cabinets, and/or a dedicated “IT” room with controlled access.
The physical layer can also be applied to the network architecture or design of the network. Traditional network design was based on a “flat” network approach where all host devices have the same access and are addressed to the same network or subnet.
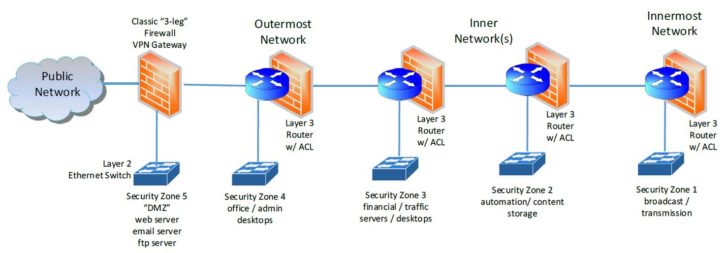
The current network design approach recommends a layered or segmented approach to the network architecture. Advantages of a segmented network design include performance enhancements and increased security. Cybersecurity advantages focus on the ability to minimize the attack surface and controlling access to hosts. In practice, the segmented network architecture approach groups hosts in functional layers based upon security priority.
The segmented network adheres to the cybersecurity principal of Defense in Depth, and is a fundamental recommendation in adopting the NIST Cybersecurity framework. If a breach should occur in the outermost network, another barrier is presented as well as limiting the reach of attack to those hosts only the compromised network.
In the case of a ransomware event, the spread of the malware is limited or contained to that individual network rather than the entire network within the organization. In practice the Virtual Local Area Network (VLAN) becomes the primary tool for implementing a segmented network architecture. The VLAN approach allows a single physical network to support multiple sub-networks or subnets. Each subnet is an isolated individual network with its own addressing assignments. At this point, there is no communications or interoperability between subnets.
If required, subnet interoperability will be added in a controlled manner by use of Layer 3 routing and Access Control List (ACL) techniques.
Upon first glance, the network illustrated would require numerous network devices to implement. In reality, this network could be built with two network devices. A firewall appliance handles the border protection, DMZ provisioning and VPN access. The remaining Ethernet switching and IP routing can be provided by a single “Layer 3 switch” with adequate port capacity. With 48-port switches being commonplace, small network needs can be met in a single device.
If additional capacity is needed, expansion can be accommodated by additional standalone Ethernet switches or use of a chassis-based switch platform with the appropriate quantity of switch port interface card(s) installed. It is important to note that a Layer 3 switch is a marketing term associated with a single network device that performs traditional Ethernet switching and IP routing on a port-by-port basis.
Going beyond the physical layer, Layer 2 or the data-link layer provides an opportunity for another layer of protection. With a VLAN-based segmented network implemented, the use of a managed Ethernet switch is implied. The managed Ethernet switch allows the custom configuration of VLANs, as well as providing several cybersecurity features.
A fundamental cybersecurity feature is Ethernet switch port security. This provides the ability to limit or restrict what host device can be attached to a switch port. A fundamental role of the Ethernet switch is to learn a host device Media Access Control (MAC) address. The MAC address is the physical address of an Ethernet-based host device and is “burned-in” the device firmware. The learned MAC address is captured from an incoming frame and stored along with the switch port number in the switch internal MAC address table or Content Addressable Memory (CAM) table.
If a foreign device should be attached to a switch port, the switch automatically responds upon detection of a foreign MAC address. A typical switch response would be to shut down or disable the port involved, drop the received Ethernet frame and send a notification that a violation has occurred.
In essence, Ethernet port security provides another barrier if physical tampering occurs and a foreign device is connected to the network switch port. A best-practice approach allows a single host to be connected to a switch port by limiting to a single MAC address per switch port. This limiting step can also help to minimize the impact of a DoS attack by preventing the Ethernet switch CAM table overflow. A switch will re-boot if a CAM table overflow should occur.
The managed Ethernet switch can provide additional security features such as Dynamic Host Control Protocol (DHCP) snooping which can detect and prevent a rogue DHCP server from being attached to the network. This could occur during a Man in the Middle cybersecurity event or simply as an accident when improperly connecting a WAP to a switch. A practical example is the connection of the WAP WAN port to a network cable rather than the LAN port, thus adding the WAP DHCP or rogue functionality to the network. DHCP snooping essentially acts as a DHCP firewall.
After Layer 2, also known as the data-link layer, Layer 3 or the network layer brings another level of protection to the network infrastructure. The network layer is associated with virtual addressing (IP address), inter-network routing and packet filtering.
Additional cybersecurity protection can be implemented through IP Security (IPsec) encryption. Interoperability between the segmented networks must be added when necessary. Layer 3 routing must be enabled to provide the desired inter-subnet communications. Routing is only added when required. If implanted, it is controlled via packet filtering through an Access Control List (ACL).
The ACL controls access to a subnet or network by performing basic packet filtering. It will permit or deny an IP packet from entering a Layer 3 device ingress interface or leaving an egress interface. The admit or deny decision is based upon a pre-defined rule that utilizes the IP layer 3 header information such as source IP address, destination IP address or protocol.
The IP address can be a single address, a logical block of IP addresses such as a subnet, as defined by the IP address subnet mask. With the additional information provided by Layer 4 or the transport layer, the decision can include port information. The transport port number is often associated with a specific service or application communication. Logical operator statements can be used in a ACL to allow logical combination of Later 3 and 4 header information to reach the permit or deny decision. Creating the ACL can be complex and time-consuming. Once in place though, it is very effective, and acts as a stateless firewall.
In addition to an ACL, a conventional Layer 3 firewall can be implemented between internal subnets. An important difference between an ACL and a conventional firewall is the stateful operation of the firewall. The firewall will in general deny incoming packets from an outside network unless an internal network host originated the conversation with the outside host. The firewall remembers the conversation through an internal table dynamically created for each conversation created. In practice the firewall will incorporate both stateless permit or deny rules such as found in an ACL, and dynamic rules that are created based upon stateful conversations where allowed.
A practical example could be an automation system in a subnet requesting the daily programming log from a traffic system located in another subnet. The ACL would allow only the two hosts to communicate via the FTP.
IP by design is not secure. To secure a network, encryption or IP Security (IPsec) must be added. IPsec is a Layer 3 encryption technique that provided secure communications between host devices. Encryption can be implemented at several levels of the OSI model, with Layer 3 or IPsec forming the foundation encryption.
It should be noted that Layer 2 encryption is possible and often utilized by the government and military applications. Layer 2 encryption is accomplished by dedicated proprietary hardware “green” boxes, and not typically found in the commercial market industries primarily due to cost.
Encryption should be used anytime a public network such as the internet is utilized for communications with another network such as remote access via a VPN. Encryption can also be used in internal networks such as a IP-based Studio-Transmitter-Link (STL) path. This is yet another method to prevent unauthorized access or disruption of information transported and/or a Man in the Middle attack to disrupt normal programming.
Encryption is also available at Layer 4 as Transport Layer Security (TLS) and at Layer 7 as application security such as Secure Sockets Layer. SSL is based upon creating an authenticated and encrypted communications link between hosts such as a user client exchange with an application server.
Protecting the host device is often complex due to the diversity and sheer number of potential devices in use. An IP host device can take on numerous forms and functions. Traditionally, a host has been a server or desktop computer. Today, the variety of possible devices is vast.
Regardless of the type, they share common characteristics and capabilities as defined by the Internet Engineering Task Force (IETF) Request for Comments (RFC)’s. IETF RFC 1122 provides the details of those capabilities.
IP hosts should be hardened to reduce or minimize the potential attack surface of the device. Necessary steps may include changing default device login information, removing any unused applications and services, deleting guest or legacy user accounts and maintaining a proactive up to date patch or update routine.
Most computer-based devices found in the broadcast plant will be derived from Microsoft Windows or Linux operating systems. Both platforms have potential vulnerabilities but can be made secure. Linux systems may offer more flexibility due to the open-source design. Windows is more of a closed system with limited flexibility.
The growing popularity of Internet of Things (IoT) devices often create unique cybersecurity challenges. An IoT host device can be one of a variety of devices found in a modem broadcast facility. Common devices include security cameras, digital signage, thermostats, card access systems and even a light bulb. From a practical standpoint, these devices must be secured externally as they often lack basic security features due to limited or minimal operating system and cost.
Due to limited resources (processor and memory), it is impossible to change defaults configurations or add cybersecurity protections such as antivirus and malware. Common practice is to place essential devices on their own subnet and utilize external packet filtering via an ACL and/or firewall to secure and control access.
Application cybersecurity protection is focused on authentication and encryption of the interaction between user and application. Authentication ensures the proper user or application has the proper access, blocking all others. Application security can be cumbersome, especially where multiple applications are involved.
An authentication system is referred to as a “single sign on” system, and can be utilized to minimize the administrative tasks associated with application security. A benefit is allowing the user access without the need to manage multiple login information.
It is common for the system to provide federated identity techniques to secure application access and identification of the user or by another application. Two-factor authentication of users is often utilized as an added level of protection beyond simple login information exchange. In some cases, three-factor techniques can be applied to add a further protection barrier.
After much planning, time and labor, everything is in place, and your network is secure. Now what?
Some would sit back and see how it works, but a more proactive approach would be to test it yourself, as Pecena explains. “Anyone operating a broadcast network should do penetration testing on a routine basis. I view the pen test as the ‘proof of performance’ of a broadcast IT system.”
Conclusions
The industry is well invested in the vast array of “IP-enabled” devices. However, it is well to question whether every host device needs to be on the network or have public network access. If so, then take the precautions to minimize the attack surface and a potential cybersecurity event.
An important consideration not addressed in Pecena’s paper is network monitoring. Best practices in network management is monitoring to ensure network operation in a proactive manner. Unusual network traffic patterns or unexplained increased in the use of resources can indicate that a cybersecurity incident is occurring. Knowing what is normal and alerting when it is not is an essential requirement of network and cybersecurity management.
All of the above is for naught if users are not educated in cybersecurity and social engineering. As cybersecurity techniques have improved, the use of phishing has increased. It only takes one careless user opening an e-mail attachment from an unknown source to bring your well-engineered system down. Training users in cybersecurity needs to be another ongoing process.
Finally, Pecena notes that the cyberattacks that we hear about are only the tip of the iceberg. “It makes headlines in the trade publications when a large broadcast group is attacked, but the mom-and-pop, middle-market and college broadcasters are also vulnerable. “These folks are regularly hit by cyberattacks which are financially devastating,” says Pecena, “but these are the stories you never hear about.”
Pacena’s Top 15
Taking adequate cybersecurity precautions can be summarized in these action steps:
- Accept there is no single solution!
- Implement multiple protections via Defense in Depth (DiD)
- Change default logins
- Use strong passwords (paraphrases)
- Separate admin and user accounts on hosts (WIN)
- Segment your network (VLAN) — reduce attack surface — create multi-layer security zones
- Limit access (users and applications) — apply “least privilege”
- Use packet filtering — control host access (ACL and/or firewall) deny by default
- Disable unused services — close ports not required
- Use secure access (SSH not telnet) and VPN for off-site access (2-factor authentication)
- Monitor your network — know what is normal
- Use “intelligent” host backup solutions — test backup restoration
- Keep systems patched
- Utilize signature-based deep-packet inspection antivirus/malware keep updated (often daily)
- Don’t overlook social engineering — engage and educate users — phishing is alive and effective












