After completing my due diligence regarding cybersecurity in my broadcast operation, I accepted that cybersecurity is a reality, whether at a small radio station or a state-of-the-art major-market station.
The migration to an information technology-based Internet Protocol network infrastructure has brought advantages to my station in system capability, flexibility, scalability and cost-effectiveness. But I realize that these advantages created exposure to potential cyberattacks and that protecting my infrastructure grows more challenging each year. I accept that cybersecurity is an essential responsibility of my role as a broadcast engineer and cannot be ignored.
I invested time in studying and I understand that cybersecurity can be a complex undertaking, as well as confusing and challenging.
My resources include the National Institute of Standards and Technology, the Cybersecurity Infrastructure Security Agency and the industry at large.
The NIST Cybersecurity Framework provides a structured set of guidelines and best practices for protecting IT assets and mitigating cybersecurity risks.
The framework is organized into the five areas of Identify, Protect, Detect, Respond and Recover. These areas are further divided into several categories and sub-categories before reaching a specific guideline or best practice, along with a discussion of its significance.
CISA offers a range of resources, from tutorials and best-practice checklists to the industry-recognized Known Exploitable Vulnerabilities of cyberthreats, or KEV. I found it beneficial in establishing a risk-based approach to prioritize my time and deployment of resources.

Core principles
During my course of study, I realized that cybersecurity is founded on certain core principles. Several of these form the guidelines and best practices that reduce risks and protect my assets.
The principle of Defense in Depth, or DiD, establishes redundant levels or layers of security controls within the IT infrastructure, such that I have no single reliance upon a single cyber precaution. If a precaution is breached or fails, another will prevent further impact.
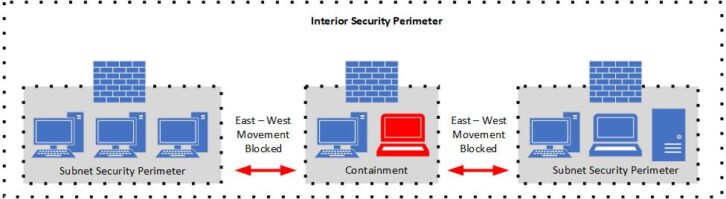
A critical aspect of DiD implementation is to have the proper network architecture. A layered or segmented network is essential. The segmented network is a traditional “flat” network compartmentalized by dividing into smaller sub-networks or subnets, each of which can have the appropriate security controls applied that fit the workflows occurring within that subnet.
I enhance security by minimizing the attack plane, providing containment if a cyber breach should occur by minimizing movement throughout the overall network. Movement throughout the network or “east-west” is a common goal of virus and ransomware malware. Network performance enhancement may result, as the reach of network service broadcasts are limited.
With a segmented network infrastructure in place, I can implement further DiD steps. These include physical infrastructure security and managed Ethernet switch security features, such as port security and packet filtering to control access.
Packet filtering is accomplished by basic Access Control List (ACL) stateless filtering of stateful filtering through a firewall. In certain situations, I may use both types of packet filtering. I can implement further security controls for encryption provided by IP Security (IPsec), Transport Layer Security (TLS) or Secure Shell (SSH). I should use encryption and Multi-Factor Authentication (MFA) for any remote access via a public network or the internet. I use a Virtual Private Network (VPN) to access my broadcast network remotely via the internet.
The principle of Least Privilege (PoLP) — often referred to as “deny by default” — is based upon limiting access rights to users and applications to the minimum level required to perform the defined business function. Limiting access to IT assets reduces the risk of abuse and propagation of a threat via “east-west” movement throughout my IT system.
Finally, the “CIA triad” is the core objective of IT security. It establishes the goals of insuring Confidentiality, Integrity and Availability of IT systems.
Confidentiality refers to the data within the IT infrastructure that is available only to authorized users and systems, whether flowing through networks, stored at rest or within a workflow process. Integrity refers to ensuring that data has not been modified, tampered with or altered. Availability ensures IT resources are available to authorized users and applications.
18 actions
From the knowledge and recommendations I gained, I developed and executed my structured cybersecurity plan based upon my specific environment. I did the following:
- Accepted there is no single cybersecurity solution
- Used DiD to provide redundant precaution implemented in a structured and coordinated manner
- Implemented a segmented network for cybersecurity protection and performance enhancement
- Inventoried my IT assets and used a risk-based approach to establish priorities
- Established physical infrastructure security measures
- Utilized Ethernet switch port security
- Used stateful and stateless packet filtering to control and limit resource access
- Applied PoLP to users and applications
- Used encryption & Multifactor Authentication (MFA) for any remote access
- Kept my network hardware and operating systems updated and current
- Changed default logins to strong & unique credentials
- Deleted stale accounts
- Disabled any host services not required or used
- Used packet filtering to block any service port if not able to be disabled
- Performed routine vulnerability and malware scans with current signature files
- Maintained critical system backups that followed the 3-2-1 rule: Have three copies of critical data, on two different types of media and one offline
- Routinely test backup systems for operability and reliability
- Established infrastructure monitoring and alerting to identify when abnormalities occur
With my cybersecurity precautions in place, I also use the tools that a malicious hacker or threat actor might employ. I want to verify that precautions I think are in place are functioning as intended. And I check again after updates are performed, because device configurations might be changed to defaults.
The basic tool used for penetration testing is a port scanner such as “nmap.” A port scanner identifies host devices visible on a network and determines services enabled by active port identification. I find online port scanning tools such as Shodan useful for quick routine checks of my public network viability.
Penetration or “pen” testing is the last step in my cybersecurity prevention plan, in which I view as my “proof of performance” of the broadcast IT system.
With a solid prevention plan in place, perhaps I should be able to forget about cybersecurity. But while I may have adequate technology-based precautions in place, ransomware delivered through social engineering tactics remains the greatest threat faced today.
NIST defines social engineering as tricking someone to reveal information or grant access by manipulation of human emotion. Social engineering is often based on manipulation of emotions with a sense of urgency to exploit a victim’s lack of knowledge, fear or curiosity.
Phishing is the most common tactic, ranging from mass user audience attempts to focused or targeted users. Attackers often use personal information to establish a relationship of trust with the targeted victim. They may learn information or trick the victim into downloading malware by using voice phone calls, SMS messaging, email and even postal service mail.
So, educating my users about the dangers of social engineering tactics is critical. And the Cyber Division of the FBI recently raised awareness of dual threats — successive ransomware attacks affecting an organization days apart.
Ransomware delivered through social engineering is a rapidly evolving area of cybersecurity shown to be effective and worthy of a future article.
Virtually all broadcast stations rely on an IT-based IP network infrastructure. The reality is that I can never forget about cybersecurity. I might rest better at night knowing that my cybersecurity plan is in place. But I remind myself that cybersecurity evolves constantly and that my protections must do so as well.
A free SBE webinar includes discussion of principles described here. Find it here.







