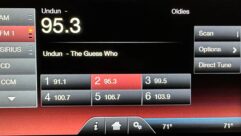
Pubcaster Michigan Radio has apologized to listeners who may have seen profane RDS messages displayed on their in-car receiver.
The RDS system was hacked from the transmitter site for WVGR(FM) and WFUM(FM), allowing someone to post unauthorized messages that were displayed on RDS-equipped receivers in the west Michigan and Flint areas, according to station Marketing Director Steve Chrypinski.
“Michigan Radio took immediate steps to address this breach as soon as we became aware of it, including updating the passwords and other security settings used to access our RDS display. We are also further encrypting our system to avoid a repeat of this incident,” says Chrypinski in a message on the station website.
The station became aware of the problem earlier in the week when listeners began calling and emailing about the issue.
Michigan Radio is licensed to the University of Michigan. The problem occurred during an inopportune time for the broadcaster, which is conducting a pledge drive.
Chrypinski apologized to listeners and said the station is working with the university’s IT department to try and find those responsible, according to MLive.
Engineers tell Radio World this situation is similar to last year’s “zombie” attack hack of a few EAS encoders/decoders. Hacking can happen to stations that have their RDS encoders on public IP/Internet connections.
Stations should practice safe networking practices and deploy RDS encoders on a VPN/WAN secured connection or use other security techniques to prevent unauthorized access to the encoders, experts say. Simply changing the username/passwords from default isn’t really good enough.